
Security Analysis & Threat Mitigation
Securing Systems & Thwarting Attacks
Today's world is rife with threats from all types of cyber criminals. To make matters worse, many types of attacks are nearly impossible to detect and even harder to avoid. One of the most subtle vectors of attack is a tactic often referred to as "Social Engineering", a concept first espoused by Kevin Mitnick, a legendary hacker who's 1995 arrest and prison sentence for various computer and communications crimes sparked a career as a well paid security consultant. His past is hardly a deterrent to the new breed to criminal hackers yet he has gained respect as an extremely intuitive security consultant.
It is very easy to neglect or fail to address security issues until it is too late. The neglect often happens when corporate IT systems grow over years or teams move on to new projects. So how does this happen? When a project is placed into production, it is nomrally subject to some form of a security audit to ensure risks are mitigated. Even if a project finishes and has completed security hardening when placed into production, a manager must take continual action to ensure periodic security reviews are done in the future as new exploits and vectors of attack become known. Unless an enterprise is regularly conducting security audits, it is very easy to become vulnerable through lack of action.
From decades of consulting work, we have developed a proven process to help businesses identify areas of security that require ongoing review and empower teams to conduct those reviews. The frameworks for these is fairly simple, yet unless implemented, cannot result in success.
Types of Security Threats
It is a good idea to understand the major categories of security issues. The following is not considered an exhaustive list and new threats appear weekly. To remain vigilant, we recommend subscribing to our security bulletins. Here are some common types of threats.
-
Malware - software that gets installed on a computer within an enterprise. There are many types of malware, commonly including
Spyware and Adware. Keystroke loggers are often in this category however they are very difficult to plant. Spyware and Adware are
most commonly used by companies engaged in questionable marketing techniques yet there are no firm boundaries.
-
Social Engineering - the practice of using real world observations of human behavior and data creates attack opportunities. Social Engineering is a
form of psychological manipulation to gain security access by tricking users into making security mistakes or relaying sensitive information. Additionally,
common patterns of human behavior (such as using "P@$$w0rd" as a password), are generally known to attackers who can drastically minimize their attack times
by applying common rules first.
-
Trojans, Viruses and Worms - these are malicious software processes that work their way into a system or environment, often replicating
and infesting other systems on the same networks. Detecting these
can be notoriously difficult as some lie dormant for months or years before being activated to perform a task.
-
Denial of Service (DOS), Distributed DOS and Botnets - rather than gain direct access to a target, this type of attack uses a strategy
of denying legitimate users access to a system or network by overwhelming it with traffic from other systems. Typically, Trojans or Worms
(above) are used to gain access to other computers that are subsequently loaded with software to launch DOS/DDOS style attacks when triggered.
Since the DOS/DDOS attacks come from multitudes of distributed systems, it makes it nearly impossible to pinpoint the origins of such attacks.
-
Intrusion/Brute Force - attacks where a system compromise is achieved via use of a blunt force type fo attack, such as sending in thousands of
concurrent login attempts guessing usernames and passwords. These are amongst the easiest intrusion attempts to detect and mitigate however some
are highly complex and use IP masquerading and random timing to hide their activities. Limiting attempts and types of data entries is a good defense.
-
Injection Attacks - the injection of executable or declarative code into the right area of a computer program can cause severe damage. Consider the
impact of an SQL statement to DELETE * FROM * exectugin on your database. Like Brute Force attacks (above), these are often easy to prevent using
common patterns.
-
Direct Hardware/Network Physical attacks - the use of mechanisms like keystroke loggers and packet sniffers to gain unauthorized access to privileged data.
In such attacks, Social engineering is usually also used to gain access to the secure area to plant the keystroke loggers or other mechanisms. Man-in-the-Middle
(MITM) attacks are sometimes used by placing proxies in the middle of sensitive networks.
-
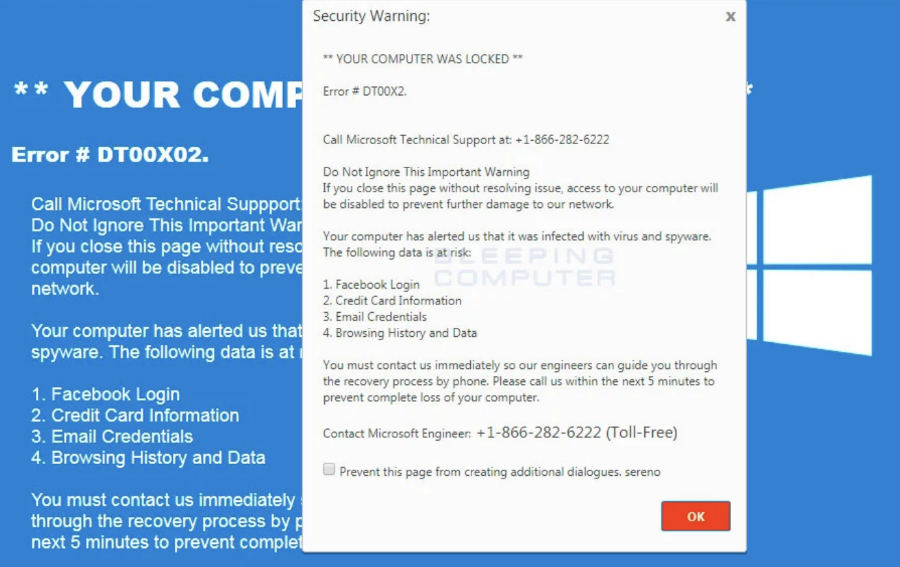
Drive-by Downloads, Scams - Clever manipulations have been performed by criminals who have compromised servers and use the server (often not their own) to
force malicious downloads or to send a message to the users screen stating that there has been a virus detected on their system and directing them to phone
a number. This is sort of a hybrid attack that uses some social engineering and if successful, results in the victim providing the perpetrator with a credit card.
This is usually done under the pretense that the perpetrators are going to fix an issue with the victims computer.
There are too many other scams and security threats to list. Every day, new threats, viruses and types of attacks emerge.
Common Goals of Attackers
Most attacks are done for financial gain. Ransomeware is a term used to denote a popular pattern of seizing files from an infected computer or server and demanding a monetary reward to their return (often using Bitcoin or other cryptocurrencies are they are notoriously difficult to track). In the fake support scam shown above, once criminals have your credit card, they can pretty much add charges to it at any time, without any further notifications to you. If you have been the victim of one of these types of attacks, report it to authorities immediately and monitor your credit card for suspicious transactions.
Others compromise systems for political or social purposes. The political angle is a popular tactic shared by many hackers loosely referred to as "anonymous" in the press. Contrary to popular belief, Anonymous is not a group nor does it have members or any structure or corpus. It is simply a tactic. If a person ever claimed to be a member of anonymous, you can be assured they do not have any idea what they are talking about. Those who subscribe to this tactic do not pay membership fees and carry Anonymous ID cards in their wallets. The opposite is true. A true practitioner of this tactic will likely feign complete ignorance about it when publicly questioned as the goal is to remain anonymous at all costs. Hackers using the anonymous manifesto have hacked computers systems in the past with goals of exposing or "outing" persons or activities the hacker believes are wrong and need to have a spotlight shined upon. These often include individuals how have wronged others, such as those who used to taunt and torture Amanda Todd, driving her to suicide. As such, some anonymous practitioners have gained a Robin Hood type status in the general community.
More complex goals of hacking are linked to global military gains and industrial espionage. As recently as 2021, a massive breach of multiple systems operated by many branches of the United States government was accomplished by hckers sneaking rogue code into a commonly used software update system. Foreign state actors were believed to be behind that attack. Many industrial and scientific knowledge espionage hacks were also noted in the past years.
Do I Need Security Consulting?
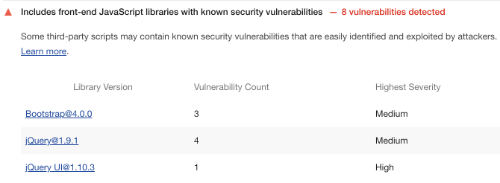
If you have a website, we recommend spending at least two hours per year to have someone review your code base to determine if you have any technology components that have known vulnerabilities. There are still millions of websites using insecure versions of jQuery and other libraries that the authors have deprecated due to security issues. Many forms are not properly secured and the code that processes form entries can be used to spam others in some cases. We can quickly identify such libraries and recommend quick replacements, often with minimal resources. The graphic below shows a very common pattern of use of jQuery 1.9, deprecated as insecure.
Our Security Work
We do not publish details of security analysis and threat assessment online as it would provide attackers with invaluable information on how to better hide their activities. We work with enterprises in strict secrecy and operate under a clock of non-disclosure.
To begin a security assessment, use the contact form on this website to start the process. We can custom tailor packages to any sized corporation or individual.
Any new clients receive a 100% free initial consultation with us. We have great packages for website security audits starting at just $199. We have Similar packages are available for mobile apps and other forms of software. Please use the contact form to begin your audit today.
